Kerberos Components
» Table of Contents | » Glossary | » Index |
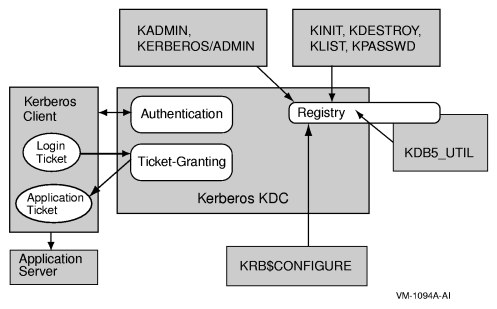
Figure 1-1 depicts the interrelationship between the various components of Kerberos.
When a client logs in to the realm, an authentication request is sent to the Kerberos Key Distribution Center (KDC). A Ticket-Granting Ticket (TGT) is returned as the result of authentication. When the client application starts, the TGT is used to request an application ticket. The application ticket is then sent to the application server, which verifies the application ticket with the KDC. Normal communication can then begin.
The Kerberos registry can be manipulated in several ways. It is initially created via the KRB$CONFIGURE command procedure. Other tools used to access the Kerberos information are:
kadmin - Used for reading or updating the Kerberos registry.
kinit - Creates credentials for a user.
klist - Displays the existing credentials for a user.
kdestroy - Deletes a user’s credentials.
kpasswd - Changes a user’s Kerberos password.
kdb5_util - Dumps or loads the Kerberos database for save and restore operations.
Each Kerberos realm will have at least one Kerberos server. This server, the Key Distribution Center, contains the Authentication Service, the Ticket-Granting Service, and the master database for Kerberos. These services are implemented as a single daemon: the KDC (KRB$KRB5KDC).
The authentication service handles user authentication, or the process of verifying that principals are correctly identified. It consists of the security server (or servers) in the KDC (or KDCs), and security clients.
A security client communicates with a security server to request information and operations. The security server accesses the registry database to perform queries and updates and to validate user logins.
Once authenticated, a principal will be granted a TGT and a ticket session key, which gives the principal the right to use the ticket. This combination of the ticket and its associated key is known as your credentials.
A principal’s credentials are stored in a credentials cache, which is often just a file in the principal’s local directory tree.
The Kerberos database contains all of the realm’s Kerberos principals, their passwords, and other administrative information about each principal.
Each KDC contains its own copy of the Kerberos database. The master KDC contains the primary copy of the database, which it propagates at regular intervals to the slave KDCs. All database changes are made on the master KDC. Slave KDCs provide ticket-granting services only, with no database administration. This allows clients to continue to obtain tickets when the master KDC is unavailable.
OpenVMS provides three different versions of each of the Kerberos user interface programs: the original UNIX® style, a DCL version, and an X Windows version. The DCL interface for the user utilities (kinit, klist, kdestroy, kpasswd) is invoked by the DCL command:
|
The DCL interface for the administrative utility (kadmin) is invoked by the DCL command:
|
Either DCL interface can be modified with an /INTERFACE qualifier to invoke the X Windows version. For example, the command line for the administrative program is as follows:
|
DCL help is available within each of the DCL interfaces.
kadmin
The kadmin program allows for the maintenance of Kerberos principals, policies, and service key tables (keytabs).
kinit
The kinit program explicitly obtains Kerberos tickets. Similarly, if a user’s Kerberos ticket expires, kinit is used to obtain a new one.
klist
The klist program displays the existing tickets for a principal and various details about those tickets, including expiration time.
kdestroy
The kdestroy program removes all of the tickets for a principal. Because Kerberos tickets can be stolen and because someone who steals a ticket can masquerade as another principal, Kerberos tickets should be destroyed when you are away from your computer.
kpasswd
The kpasswd program changes a Kerberos principal’s password. Passwords should be changed periodically.
kdb5_util
The kdb5_util program creates, destroys, dumps, and loads the Kerberos database. It also allows the creation of a key stash file, which allows a KDC to authenticate itself to the database utilities. Unlike the Kerberos utility programs (with the exception of kadmin), access to kdb5_util is generally limited to Kerberos administrators.
kprop
The kprop program propagates the master KDC database to slave KDC servers.
ktutil
The ktutil command invokes a menu from which an administrator can read, write, or edit entries in a Kerberos V5 keytab or V4 srvtab file.